“It's Not What We Were Trying to Get At, but I Think Maybe It Should Be”: Learning How to Do Trauma-Informed Design with a Data Donation Platform for Online Dating Sexual Violence
DOI: https://doi.org/10.1145/3613904.3642045
CHI '24: Proceedings of the CHI Conference on Human Factors in Computing Systems, Honolulu, HI, USA, May 2024
A majority of people experience trauma, spurring calls to incorporate trauma-informed approaches (TIA) from public health and social work into technology design. While technologies touted as trauma-informed are starting to propagate the literature, there persists a gap in knowledge around how design teams apply TIA and qualify their technology as adhering to trauma-informed principles. We address this through a 12-month development project with trauma and sexual violence experts to produce Ube, a data donation platform for collecting online dating sexual consent data to improve sexual risk detection AI. Through analysis of design documentation we retrospectively articulate a trauma-informed design process that evolved through the course of Ube’s development, comprising three elements for integrating trauma-informed principles: design goals that adapt the definition of TIA to the application domain, design activities that map to trauma-informed principles, and consequent design choices. We conclude with methodological recommendations to improve trauma-informed design processes.
ACM Reference Format:
Wenqi Zheng, Emma Walquist, Isha Datey, Xiangyu Zhou, Kelly Berishaj, Melissa Mcdonald, Michele Parkhill, Dongxiao Zhu, and Douglas Zytko. 2024. “It's Not What We Were Trying to Get At, but I Think Maybe It Should Be”: Learning How to Do Trauma-Informed Design with a Data Donation Platform for Online Dating Sexual Violence. In Proceedings of the CHI Conference on Human Factors in Computing Systems (CHI '24), May 11--16, 2024, Honolulu, HI, USA. ACM, New York, NY, USA 15 Pages. https://doi.org/10.1145/3613904.3642045
1 INTRODUCTION
Trauma is the adverse effect on an individual's mental, physical, or emotional well-being as a result of distressing experiences such as disaster, violence, or abuse [45]. Trauma has been foregrounded in HCI in various ways, even if the term is not always explicitly used, such as examining harms through computer-mediated communication that are commonly associated with trauma [33, 54, 88, 103], directly engaging with stakeholders about experiences that may have been traumatic [38, 93, 95], and broaching new technology that may address the effects of trauma [1, 20, 56, 80, 90, 102].
The field is still in early stages of learning how to formally incorporate trauma in technology design. In recent years HCI scholars have encouraged use of the trauma-informed approach (TIA) [2, 24, 34], a well-established framework from the Health and Human Services domain for providing care and support to individuals who have experienced trauma [45]. TIA is grounded in four assumptions about the administering organization or system: that it can Realize the impact of trauma; Recognize signs and symptoms of trauma; Respond to trauma in practice; and actively Resist re-traumatization. Implementations of TIA are guided by six principles: safety; trustworthiness & transparency; peer support; collaboration; empowerment, voice, and choice; and sensitivity to cultural, historical, & gender issues [45].
TIA has traditionally been discussed in regards to behavioral health services (e.g., clinical care) rather than technological artifacts; authorities on TIA consequently advocate for "TIA adaptation in different settings or for a particular population" through "terminology and practices appropriate to that setting or set of individuals served" [45]. This adaptation has been spearheaded in HCI by Chen and colleagues’ tailoring of the six trauma-informed principles to computing [24], as well as various sets of trauma-informed design guidelines for specific computing technologies including social media platforms [84], post-trauma self-regulation apps [98], and technologies for social-emotional learning [1, 56].
While technologies touted as products of trauma-informed approaches are starting to propagate the literature [47, 72, 83] there persists a gap in knowledge around how trauma-informed design teams apply a trauma-informed approach and qualify their resultant technologies as adhering to trauma-informed principles. Dialogue around trauma-informed design processes is essential, not only to progress the field's collective understanding of how trauma-informed principles have been - and could be - integrated into technological artifacts, but to allow scrutiny into how the "trauma-informed" label is applied to technology.
The research question motivating this paper is: How does a trauma-informed design team qualify their resultant technology as adhering to trauma-informed principles? What are the design practices and decision-making processes that lead to that designation? We explore this question through a 12-month trauma-informed development cycle with an interdisciplinary team spanning nursing, psychology, HCI, and AI to produce Ube: a data donation platform for collecting online-dating sexual experience data to enable novel forms of sexual risk detection AI. Data donation refers to voluntary contribution of data [40, 86], often through dedicated applications [5, 8, 31, 40, 46, 74], to amass ecologically valid datasets for training AI. Because we are asking online daters for data about experiences that could be associated with trauma, the very act of donating data can be (re-)traumatizing, posing opportunity for trauma-informed design.
Our analysis unpacks a trauma-informed design process that began with a shared intent and baseline design strategy to protect data donors from (re-)traumatization, which evolved over the 12-month development cycle to more explicitly integrate a TIA through emergent and iterative design practices. We used reflexive thematic analysis [18] to make a retrospective mapping of our evolving design practices, culminating in articulation of three key procedural elements to integrating a TIA into our technology design: 1) design goals shared by the team that seek to adapt the four assumptions of TIA to the specific application area, in effect asking what it would mean for the resultant technology to realize, recognize, respond to, and resist (re-)traumatization; 2) design activities reflective of specific trauma-informed principles; and 3) resultant design decisions or interface features that are scrutinized in their perceived adherence to the trauma-informed principles they stemmed from. Our findings section details the design goals, activities, and decisions specific to our use case of data donation to illustrate this process. Afterwards we reflect on our adhoc methodological choices to aid in transferability and improvement of our trauma-informed design process to other application areas.
2 BACKGROUND
2.1 Trauma and The Trauma-Informed Approach
Over two-thirds of the global population have experienced trauma at least once in their lifetime [61]. Trauma is defined as "lasting adverse effects on the individual's functioning and mental, physical, social, emotional, or spiritual well-being" resulting "from an event, series of events, or a set of circumstances an individual experiences as physically or emotionally harmful or threatening" [45]. Trauma's impact on health can be profound and multifaceted, leading to both immediate and long-term physical, psychological, and emotional consequences, including increased susceptibility to chronic illness [42], mental health disorders like PTSD and depression [50, 57, 100], and decreases in life satisfaction [15, 78, 94].
As awareness of trauma and its health impacts has grown, healthcare organizations have come to recognize the need for trauma-informed care [58, 65, 99]. The most common form of trauma-informed care, known as the Trauma-Informed Approach (TIA), was established by the Substance Abuse and Mental Health Services Administration (SAMHSA) [45]) with the goal of creating a safer environment for the care team and persons they serve. TIA necessitates capacity to satisfy four assumptions (the "four R's"): A program, organization, or system that is trauma-informed realizes the widespread impact of trauma and understands potential paths for recovery; recognizes the signs and symptoms of trauma in clients, families, staff, and others involved with the system; and responds by fully integrating knowledge about trauma into policies, procedures, and practices, and seeks to actively resist re-traumatization [45] (bold added).
SAMHSA outlines six principles for guiding organizational development as well as interventions and interactions with individuals who have experienced trauma, emphasizing that these principles should be viewed not as a rigid checklist, but as sensitizing concepts that inform and shape practice [45, 84]. (1) Safety: Recipients as well as providers of trauma-informed services feel physically and psychologically safe. The setting and interpersonal interactions instill a sense of safety through the trauma-informed organization/system adhering to confidentiality and setting clear boundaries with their roles to maximize recipients’ control and choice over their experiences [35] (p. 466-467). (2) Trustworthiness and Transparency: Safety and trustworthiness are considered mutually dependent. Trust is consciously built and maintained between providers and recipients of trauma-informed services. Recommended steps for building trust involve giving "full and accurate information" and maintaining transparency about "organizational operations and decisions" [82]. (3) Peer Support: "Peer" is defined in TIA as any individual who has experienced trauma, originally derived from Shery Mead's Intentional Peer Support [60]. Peer support is recognized as key to safety, hope, and trust; it is described as the building of mutual, healing relationships among equals. Peer support should be voluntary, non-judgmental, and empathetic. (4) Collaboration and Mutuality: Collaboration is rooted in the recognition that healing happens in relationships and emphasizes the sharing of power and decision-making. It necessitates an awareness of power dynamics between providers and recipients of trauma-informed services and a response to it through identification of barriers to power-sharing and inclusion of all stakeholders in decision-making about their care pursuant to more equitable power distribution [55]. (5) Empowerment, Voice, and Choice: This principle hinges on recognizing and building upon each individual's experiences, whether it is providers or recipients of trauma-informed services. The uniqueness of every person's experiences is appreciated, and deliberate steps are taken to foster empowerment rooted in the belief that all parties have the ability to recover from trauma. Support is given to individuals’ voices and choices during care, along with shared decision-making to cultivate self-advocacy skills [17]. (6) Cultural, Historical, and Gender Issues: This principle acknowledges that trauma is context-specific, intersecting with historical issues on the basis of gender (see [14] as an example of engaging women in trauma-informed peer support), race, ethnicity, sexual orientation, age, and so on. This principle necessitates effort to move beyond stereotypes related to identity characteristics through responsiveness to, and accurate understanding of, historical trauma.
2.2 Trauma-Informed Computing
HCI research has intersected with trauma in various ways, although not always by explicitly using the term trauma. Some of this work has engaged directly with demographic groups known to experience elevated rates of personal and cultural trauma, including the LGBTQIA+ community [36, 62], people of color [36, 62], incarcerated individuals [63, 66], and sex workers [12, 81, 88]. HCI researchers have also extensively explored interpersonal harms and other life experiences that are commonly associated with trauma, including sexual [76, 103] and domestic violence [38], child abuse [23], pregnancy loss [6], and depression [96]. Other work has studied the use, design, and application of technology in response to experiences that may have been traumatic, such as the use of social media [7, 76] and chatbots [67] for social support, as well as development of games and other technologies to help children with trauma [56, 80].
Recent literature at CHI and related venues has begun exploring the formal integration of trauma into HCI research methodologies and technology design processes. Some approaches are adjacent to TIA, such as healing justice [92] and transformative justice [71] frameworks. Others more directly utilize TIA, such the application of TIA to semi-structured interviewing methods [44, 73]. Responding to calls for further investigation into "trauma-informed design" [2], Chen and colleagues [24] adapted SAMHSA's six principles of TIA into a trauma-informed computing framework and extensively outlined opportunities for applying TIA to facets of HCI including (1) UX research and design, (2) security and privacy, (3) artificial intelligence, and (4) organizational culture. Amongst UX research and design is the recommendation to minimize re-traumatization by opting not to directly interact with primary stakeholders/users during design and to explore alternative stakeholders and data in UX research - a recommendation supported by other trauma-informed design literature [1] through use of proxies, or secondary stakeholders with ample experience interacting with anticipated users.
At a more granular level the literature has presented various sets of trauma-informed guidelines for the design of specific technologies. For example, Scott and colleagues [84] offer a comprehensive overview of social media-based trauma and propose the notion of trauma-informed social media. Building on trauma-informed computing by Chen et al. [18], they speculate on how the six principles of TIA could be integrated into social media design and content moderation practices, as well as company culture. Other work involves interview studies and workshops with applicable stakeholders to produce trauma-informed design guidance. For instance, Venkatasubramanian and Ranalli [98] conducted interviews with health practitioners to gather design ideas and suggestions for post-trauma self-regulation apps tailored to individuals with Intellectual and Developmental Disabilities. The insights gained from these interviews informed discussion on the suitability and integration of trauma-informed principles into app design. Additionally, through workshops with care providers and guardians, Ahmadpour et al. [1] collected insights from proxy stakeholders to inform technology design and research methods for Social-Emotional Learning (SEL) of children with trauma. Their findings led to the creation of a safety, connection, and reflection framework along with specific guidelines for designing the SEL journey, which aligned closely with TIA assumptions and principles.
While the aforementioned guidelines have yet to be applied and validated through completed technology development processes (to our knowledge), other literature describes some developed technologies as trauma-informed. Kelly and colleagues [47] developed a web portal for university students to find informational resources, in accordance with a list of trauma-informed design heuristics they created that could then be used to evaluate usability [41]. Rajan and colleagues [72] presented Callisto, a sexual assault reporting platform, and illustrated how the cryptographic components of its system serve as roots of trust for privacy preservation. While their work did not explicitly apply TIA assumptions and principles, their findings concluded that incorporating trauma-informed technical design with data privacy is essential for creating an accessible, secure, and empowering user experience. Saxena and Guha conducted participatory design around an algorithm for child-welfare cases based on trauma-informed care [83]. The algorithm was described as being crafted from a trauma-informed perspective to enhance understanding of children and parents, and to empower caseworkers by actively involving them in the co-design process.
An important next step for building on this expansive, yet formative, work into trauma-informed design is not only additional examples of trauma-informed technologies, but documentation and retrospection on how TIA was integrated into their development to provide methodological insight to future trauma-informed design and development teams.
2.3 Sexual Risk Detection AI and Data Donation
Our focal context for applying TIA to computing is data donation platforms that can enable novel implementations of sexual risk detection AI. Use of dating apps is a well-known risk factor for sexual violence [68, 97, 103]. Research indicates that dating apps contribute to 10% of overall rapes in some samples [70, 79], with other work finding users to be 2.13 times more likely to be sexually abused than non-users [25]. Despite the prevalence of harm through online dating (33% of users have experienced harm as of 2022 [26]), features for harm mitigation are relatively underdeveloped [30, 105]. Dating apps such as Tinder and Bumble have recently deployed AI-based features for detecting harassing messages and unsolicited nude imagery [21, 91]. Yet there is a conspicuous gap of AI-driven solutions to physical sexual harm between online daters, such as when they meet for face-to-face dates [4].
Previous efforts into AI for detecting harm on social media platforms have heavily relied on publicly available data and data annotation from third parties [77]. These practices, however, raise questions about the validity of ground truth based on such annotation and suggest the need for involvement of primary stakeholders who have experienced the harms aiming to be detected (see [48, 77] for systematic reviews on risk detection AI that elaborate on this argument). Data donation has emerged as a human-centered approach for amassing ecologically valid data [64, 86], including in HCI venues [40] for improving risk detection AI [3, 5, 9, 74].
There are two different definitions of data donation in the literature. One conceptualizes it strictly as consensual transfer of personal data [86], whereas the other conceptualizes it as the consensual transfer of data as well as post-donation participation to interpret, make sense of, or label one's data: a step called data contextualization [40]. Data donation is still in formative stages, and early contexts have often involved intimate or sensitive data [41] that could be symbolic of traumatic experience, such as examples of medical and health data donation [13, 59, 85, 89] including clinical patient records [53], menstrual tracking data [40], and COVID 19-related data [32]. Most pertinent to our subject area of online-to-offline sexual violence, data donation platforms have also been developed to collect and contextualize data about harassment in private messaging interactions on social media [74] which has enabled new implementations of online risk detection AI [5] and insight into online harm [3]. The importance of donor well-being and safety has been acknowledged in the data donation literature [10], however TIA has not been formally recommended or applied to data donation platform design to our knowledge.
3 UBE: DATA DONATION PLATFORM DESIGN OVERVIEW
We created a data donation platform called Ube for adult users of dating apps to recurrently donate data about their sexual experiences with other online daters. Ube is the first artifact in a broader project seeking to produce AI-driven technologies for sexual violence prevention in online dating. These technologies focus on consent practices - how agreement to sexual activity is given and (perceived to be) received - with the ultimate goal of scaffolding or encouraging unambiguous consent exchange so as to mitigate unintentional harm. See [103, 104] for examples of how consent practices in online dating predispose users to unintentional harm.
Most immediately, the purpose of Ube is to collect trace data [9] of computer-mediated communication (CMC) that demonstrates the role of dating apps and other CMC platforms in shaping how individuals understand and give agreement to sexual activity. The creation of Ube became an essential step to amass datasets representative of consensual and nonconsensual sexual experiences between online daters, and their consent practices, for training myriad AI interventions planned by our team (for criticism over the dearth of ecologically valid datasets for training sexual risk detection AI see [77]). Expected utility of the data donated through Ube includes detection of unwanted sexual messages as well as intervention in behaviors that are antecedent of nonconsensual sexual acts. An example of the latter is a datafied retrospection interface for one's sexual consent behavior that would allow an online dater to compare their consent practices to those promoted by public health agencies and identify opportunities to modify behavior to avoid inadvertent harm. This draws comparisons to personalized normative feedback applications used for other public health issues such as alcohol consumption [69].
Technical Development:
Ube is an Android application developed using React Native and JavaScript, with dependencies managed through NPM. Ube is not an add-on to any existing data app, but rather a separately installed application that supports donation of data representing sexual experiences through any dating app.
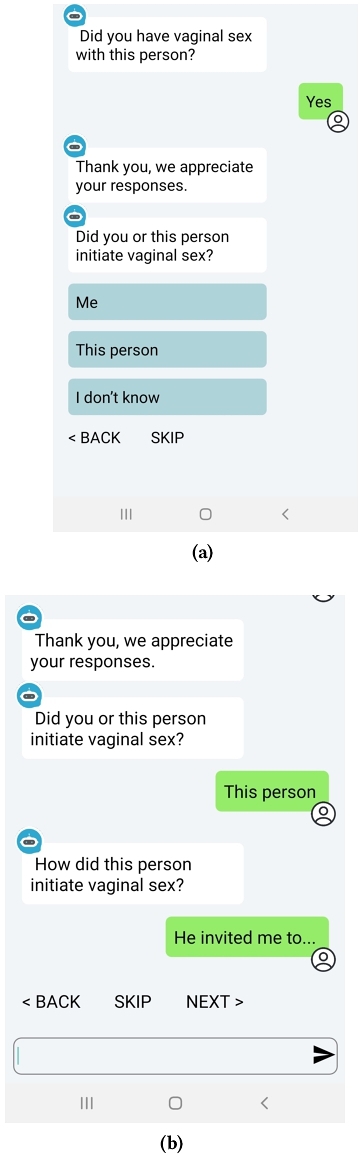
Data donation and contextualization process: Data donation through Ube is intended as a recurrent activity for online daters over a multi-month period to capture changes in one's sexual consent practices and sexual experiences through dating app-use. Any one session of interacting with Ube is intended to have a user report in detail about their most recent online dating sexual experience. Donors interact with Ube through a chatbot, which helps users identify an experience for donation by asking a series of questions about whether they met any online daters face-to-face since their last donation, and if physical sexual activity occurred. If the user did not have any in-person meetings they are asked questions to determine if any cybersexual activities occurred or were attempted (e.g., video chats of a sexual nature, sending/receiving nude images).
We follow Ortega and colleagues’ definition of data donation [40], which comprises two actions: uploading data and providing contextual details about the data (contextualization). In Ube, data contextualization occurs first, with questions about the respective sexual experience in reverse chronological order: 1) the specific sexual act that occurred or was attempted, followed by 2) how the act was initiated, then 3) if/how the donor knew the other person wanted the sexual act and if/how they conveyed their own desire for the sexual act, and finally 4) the role that the dating app and/or other CMC platforms played in understanding the other person's desire for and consent to the sexual act as well as conveying one's own desire for and consent to the sexual act. Contextualization questions can be answered either with text or voice recordings which are converted from speech to text. See Figure 1 for a selection of contextualization questions about vaginal sex; other sexual acts such as anal and oral sex are also inquired about.
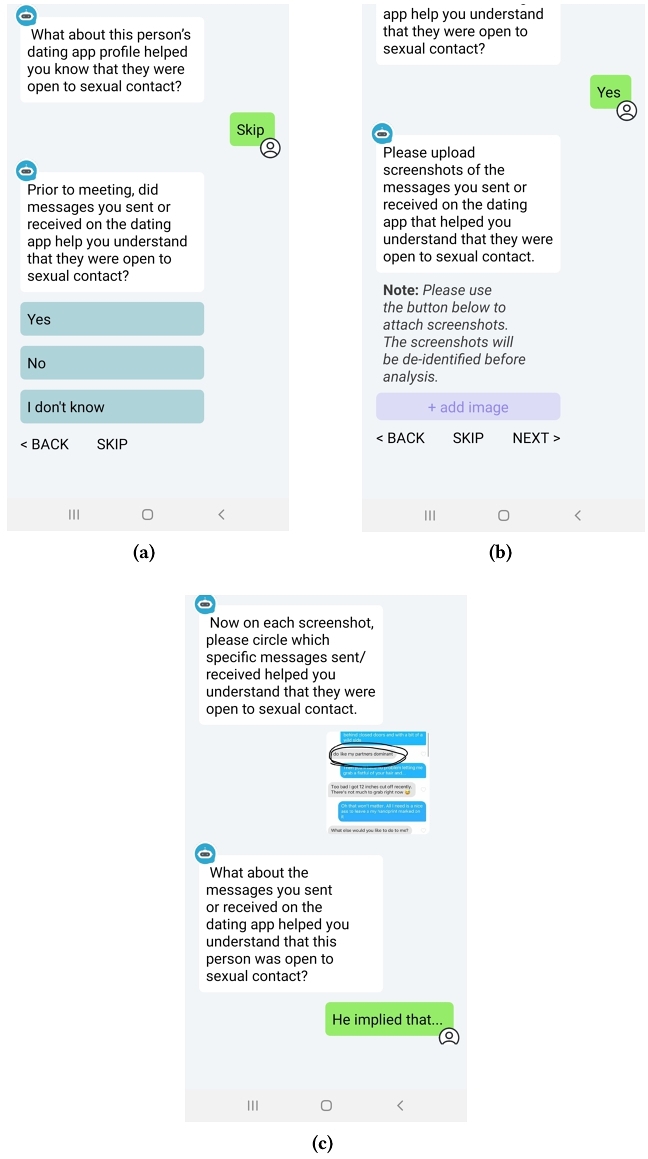
Reflective of Ube’s primary goal of amassing understanding of the role of CMC in consent practices, data donation comprises screenshots of profile pages, pictures, and messaging interactions from the dating app and/or other CMC platforms that were perceived to convey or inform desire for and consent to the eventual sexual act.
Figure
2
depicts a process of donating a messaging interaction that was relevant to the donor's perception about another person's consent to vaginal sexual activity that later occurred during a face-to-face meeting (the specification of the sexual act would have happened in previously answered contextualization questions).
4 METHODOLOGY
We engaged in a 12-month Research through Design process [101] culminating in the development of Ube as a fully functional app and thematic analysis of Ube’s design documentation to answer our research question.
4.1 Positionality Statement
Per guidance in the TIA literature [45], our design and development team featured a "champion" with a "dedicated role of instilling trauma-informed principles and practices" in the team - NURSE1 served in this role, a certified sexual assault nurse examiner (SANE) with 13 years of clinical practice and who also teaches trauma-informed care at a local university as director of its Forensic Nursing program. In addition to NURSE1, we recruited two additional "proxies" [1, 28] with intimate knowledge of individuals who have experienced sexual violence: SHELTER1-2, sexual and domestic violence shelter workers with seven and ten years of practice respectively. For expertise in human subjects research with people who have experienced or perpetrated sexual violence the team featured PSYCH1-2, both associate professors in psychology with over two decades of research examining risk factors of perpetrating violence against women and women's fear of rape; PSYCH2 is also a co-founder of the Violence and Abuse Resource Consortium for her local community. The user experience (UX) design of Ube was led by UX1 who directs their institution's human-centered design program and has published on computer-mediated sexual violence, consent, and online dating harm in HCI venues through research that involved direct interaction with participants who self-identified as having experienced sexual violence or who engaged in sexual activity without asking for consent. UX design and research was assisted by UX2-3, both graduate students with academic backgrounds in psychology specializing in sexual aggression. Technical development of Ube was supervised by AI1, a Founding Director of the AI Research Initiative at their university with expertise in machine learning for health contexts, and AI2, a graduate student and software developer working in trustworthy AI and safety of large language models (LLMs). Formation of the interdisciplinary team began with UX1 initiating a collaboration with PSYCH1-2 and NURSE1 - who at the time all worked at the same institution - to synthesize their respective research agendas on sexual violence mitigation; subsequent team members were identified and added to fill necessary roles.
4.2 Designing and Developing Ube
The 12-month development cycle began with weekly meetings amongst UX1-3, NURSE1, and PSYCH1-2 to share professional experiences engaging with people who have experienced or perpetrated sexual violence either through clinical practice or human subjects research. The purpose of these meetings, which spanned months 1-2, was to clarify the scope of online dating sexual experience data to be donated and contextualized, identify where/how Ube may predispose donors to re-traumatization, and to share best practices and experiences of interacting with people who have experienced sexual violence. These discussions evolved into documentation of text-based data donation "scenarios" in months 3-4, which elucidated the precise order and wording of questions and data donation prompts that a donor would receive contingent on the sexual experience being reported.
The text-based data donation scenarios were gradually transformed into static mockups of the Ube interface in Figma by UX2-3 in months 5-6 to motivate further reflection and iteration amongst the team, especially for interface elements that went beyond wording of donation/contextualization questions (e.g., placement of data upload boxes). Individual interface mockups were reviewed and discussed in weekly meetings with the software development stakeholders (AI1 and AI2) - their first official participation in design. This step culminated in mockups depicting every possible screen that a user could visit in Ube and key path scenarios demonstrating how and why they would arrive at that screen.
In months 7-8 the team was joined by two sexual and domestic violence shelter workers (SHELTER1-2) for six rounds of cognitive walkthroughs [87] of a low fidelity Ube prototype, each 2-3 hours long, with UX2 and UX3 serving as moderators. While traditional cognitive walkthroughs focus on how likely a user is to understand how to complete a task, our walkthroughs also focused on identifying opportunities for re-traumatization or other violations of trauma-informed principles. A seventh cognitive walkthrough was conducted between UX2-3 and AI1-2 to validate technical feasibility of the Ube prototype.
Development of Ube as an Android application began as early as month 5, and intensified from months 7-12 as interface designs were solidified. Development progress was assessed biweekly with all team members except SHELTER1-2, along with iterative testing of the Android application prototype by team members to identify bugs and inconsistencies with the Figma-based key path scenarios. Because of disparate familiarity with TIA amongst team members, weekly meetings in months 7-12 discussed TIA more explicitly, including tutorials and shared documents on TIA from NURSE1 and conscious reflections on how the TIA principles are enacted in Ube’s design.
4.3 Data Collection
Documentation of Research through Design can take many forms [11]. See Supplementary Materials for an example of each of our data sources subjected to analysis. Regarding Ube’s design, data sources include: (1) text-based key path scenarios that elucidate every data donation and contextualization prompt/question asked of the user, organized for each possible type of sexual experience being reported; (2) an Ube prototype created in Figma that includes every interface mockup in the order it would be engaged with per each text-based scenario, with embedded button-click functionality to enable simple navigation through the prototype; and (3) a fully functional Ube application for Android.
Data sources reflecting discussion of Ube’s design include: (4) weekly meeting notes over the 12-month design process, which were text-based documents constructed during meetings to log discussion about Ube’s evolving design. In early months these included formative design ideas and, later, key design decisions to relay to our software developers. After the cognitive walkthroughs these pertained to debates and conclusions over how Ube’s design does or should adhere to TIA principles. Also included were (5) video recordings and transcripts of seven cognitive walkthroughs of Ube, each with a duration of two or three hours; and (6) notes files for each of the seven cognitive walkthroughs following Spencer's cognitive walkthrough notetaking structure [87].
4.4 Data Analysis
We subjected the aforementioned data to reflexive thematic analysis (RTA) according to [18] to answer our research question about how our team integrated TIA into Ube’s design. There are three reasons we chose RTA. Flexibility in data sources: our project features several different data sources and RTA has been proven to be well suited to diverse data types such as diaries, videos, pictures, voicemails, researcher notes, and field notes [16, 19]. Theoretical flexibility: RTA allows for deductive orientation to data and therefore the freedom to apply a theoretical framework during analysis [18]; for us this was TIA. Lastly are the research questions that RTA can answer: literature argues that RTA is under-utilized when applied strictly to phenomenological inquiries [19] (p. 850). It is also well suited to “critical constructionist interrogations of meaning” (p. 850) and associated research questions that explore latent values and views on a particular phenomena - in our case, explicit and implicit views on how a trauma-informed design team determines a technology to adhere to trauma-informed principles.
4.4.1 Conduct of Reflexive Thematic Analysis. RTA is comprised of six steps [18]: familiarization with the data; coding; generating initial themes; developing and reviewing themes; refining, defining and naming themes; and writing up the results. In month 9, UX2-3 began engaging in familiarization concurrently (step 1), through individual review of the myriad data sources and casual note taking that became topics for discussion between them in informal meetings and during scheduled weekly meetings with the broader team. UX2-3 then practiced collaborative coding [18] (step 2), a reflexive exercise that involves regularly coding together while also discussing and reflecting on the coding decisions. Coding was predominantly inductive at the start, with heavy use of semantic labels for design documentation notes and cognitive walkthrough dialogue around specific features of Ube’s interface; for instance: coding several quotes from a cognitive walkthrough with "main menu" because they pertained to features accessible through the menu button. Codes for trauma-informed principles began to be used here to reflect explicit reference to the wording of some principles from design activities and meetings (e.g., "support" and "safety").
Coding progressed into an initial thematic map (step 3) of Ube’s features and associated rationale or debate for each feature, including semantic labels for trauma-informed principles. These early thematic maps were subjected to extensive critique in weekly team meetings (steps 4-5) around how TIA was reflected in the mapping, prompting a recoding of data by UX1-3 around the trauma-informed principles where a link between the principles and design activities, rather than interface features produced through the activities, became more apparent. Subsequent thematic maps were the subject of continued discussion in team meetings, which often led to further changes to Ube’s design due to identification of opportunities to better adhere to trauma-informed principles, or disagreements over whether a respective feature actually adhered to a principle. It was common at this stage for team members to point out seemingly "superficial" claims of a trauma-informed principle being reflected in a design choice, which led to either a design change or omission of the feature from the latest thematic map. Analysis and coding of data became a recursive exercise during these stages because meetings to discuss prototypical thematic maps produced their own meeting notes which were further incorporated into coding and theme review. Refinement of themes eventually progressed past a mapping of design activities, design choices, and trauma-informed principles to also include "design goals" as a way to group design activities together. These were further developed to express their own latent connections to the four assumptions of TIA, which were continually mentioned in design documentation but not explicitly incorporated in the thematic map until step 5. The thematic map and wording of key themes were solidified in step 6 (writing up), which incorporated feedback from anonymous reviewers of this paper during the revise & resubmit process.
5 FINDINGS
The outcome of our analysis was a trauma-informed design process that elucidates how trauma-informed principles were incorporated into Ube’s interface design. We position this process as the product of thematic analysis because much of it was emergent and responsive to ongoing development. Whereas the Method section reports a chronological, matter-of-fact recounting of the 12-month development cycle, it was during RTA and associated team meetings in the latter months that a coherent mapping of evolving practices for incorporating trauma-informed principles into design became retrospectively apparent. The resultant thematic map comprised three elements: design goals, design activities, and design choices.
1) Design goals adapt the assumptions of a trauma-informed "program, organization, or system" [45] to the specific application area. In effect, creating design goals entailed the team collectively deciding what it would mean for our data donation platform Ube to exemplify baseline capacity to be trauma-informed. We used SAMHSA's version of TIA assumptions (the "four R's") [45] in our team meetings by recommendation of NURSE1: capacity to Realize the impact of trauma, Recognize the signs and symptoms of trauma, Respond to trauma, and Resist re-traumatization. We pursued four design goals for Ube which were partially implicit through design activities and design documentation before being explicitly written and confirmed during RTA: Realizing the traumatic impact that data donation itself may have on the donor; supporting a plurality of data donation journeys to enable Ube to Recognize and Respond to potentially traumatic experience being reported; Resisting re-traumatization by avoiding labeling of donated sexual experiences as sexual violence; and Resisting re-traumatization through user autonomy over the data they donate.
The design goals were pursued through 2) design activities that mapped to the six trauma-informed principles, which in turn produced 3) design decisions or interface features that were scrutinized and improved in their perceived adherence to the respective trauma-informed principle. In other words, the six trauma-informed principles did not manifest through interface design choices directly (e.g., "what features can we make that adhere to the ’peer support’ principle?"), but rather through design activities. For example, we engaged in the design activity of "identifying trauma resources that data donors may need access to" which we mapped to the trauma-informed principles of safety and collaboration & mutuality, culminating in interface features for mental health check-ins (to determine if/when to provide resources) and resource pages that succinctly provide and explain each available resource. Some of the mappings between design activities and trauma-informed principles were explicitly acknowledged prior to or during the respective activity through design documentation and cognitive walkthrough transcripts, whereas other mappings were more latent and elucidated during the coding and theme generation stages of RTA.
5.1 Design Goal 1: Support a Plurality of Data Donation Journeys
TIA assumptions adapted: Recognize and Respond to trauma. The term "data donation journey" refers to a user/donor's holistic process of donating and contextualizing data [40]. One of the earliest recognitions in team meetings was that Ube would not be able to recognize potential trauma that may be associated with a given sexual experience being reported, and subsequently respond to that trauma appropriately, if all users followed the same data donation journey. Team meetings in months 1-3 put an emphasis on "flexibility" in how users progress through prompts to donate and contextualize data about their sexual consent practices to help Ube determine if and how to respond to potential trauma surrounding the respective sexual experience. We engaged in two design activities to realize this goal.
5.1.1 Identify different stakeholder types that may necessitate fundamentally different data donation journeys. Before any interface design began we dedicated several team meetings to discussing the different types of stakeholders that may choose to donate data. This stakeholder-identification exercise helped us foreground several cultural, historical, and gender issues (trauma-informed principle #6) around sexual violence that would necessitate fundamentally different flows for data donation. These stakeholder types varied based on: 1) whether the donated experience happened online or in person, 2) the presence of consent in the donated experience (consensual or nonconsensual sexual act), and 3) recognition of experience (do they self-identify as victim, perpetrator, consensual partner, or someone unsure about whether the experience was consensual). Our team members traded and discussed literature showing how sexual violence often occurs without conscious awareness due to problematic social and sexual scripts (e.g., [22]) that can lead to perceptions that sex is "supposed to" or obligated to happen in certain contexts (e.g., inviting a person to one's college dorm room late at night) [43]. These discussions helped our team recognize that prompts for data donation and contextualization that explicitly ask about "sexual violence" or "nonconsensual sexual acts" may overlook vital experiences that donors do not consciously recognize as harmful.
5.1.2 Draft key path scenarios to recognize and prepare for all possible data donation journeys. Once we identified our stakeholder types we produced 12 key path scenarios representing the fundamentally different sexual experiences that would warrant unique data donation journeys; see Supplementary Materials for a complete list (e.g, (1) Other person attempted to initiate sexual act, donor did not want it, sex did not happen). Key path scenarios [27] depict a sequential order of interface mockups that a user would interact with to achieve a particular goal. We started this process by drafting only the text of data donation and contextualization prompts. After iterations in the wording we continued onto drafting the foundational interface design patterns such as menu and button placement.
We aligned this key path construction phase with trauma-informed principle #5 (empowerment, voice, and choice) because it sought to ensure that donors are given prompts that are most applicable to their experience, thus fully enabling contextualization of relevant details. Given the variety of key path scenarios, and associated differences in donation/contextualization prompts, we designed data donation journeys as sequential processes of disclosure to ensure donors were shown appropriate prompts for their experience - this is why Ube was ultimately designed as a chatbot. For instance, a prompt such as "What about your Tinder profile expressed that you were open to engaging in sexual contact?" would only be shown to a donor who had previously acknowledged having been open to sexual contact, enabling them to talk with specificity about different strategies for expressing their openness.
5.2 Design Goal 2: Avoid Inadvertent Labeling of Sexual Experiences as Sexual Violence
TIA assumption adapted: Resist (re-)traumatization. A frequent point of discussion and debate, particularly in cognitive walkthroughs, was over Ube’s role in re-traumatization: the reliving of stress reactions related to a prior traumatic event [29]. We identified the likely reasons for re-traumatization being rooted in the wording of data donation and contextualization prompts to users - how "Ube discusses sexual experiences" with users. A goal underlying the drafting and revising of such prompts was avoidance of researcher "labeling" of donors’ sexual experiences, aiming to avoid situations where a donor may reflexively label themselves as either a perpetrator or victim, invoking self-blame.
5.2.1 Scrutinize design for opportunities to use behaviorally specific wording to avoid victim blaming and inadvertent accusations toward donors. When crafting and revising key path scenarios PSYCH1-2, NURSE1, and SHELTER1-2 all instructed that phrasing of any dialogue between Ube and the user about their sexual experiences should use behaviorally-specific wording, or reference to (potential) incidents of sexual violence through objective descriptions of the behavior rather than with the term itself. PSYCH1-2 explained that the practice is heavily used in Psychology research with participants who have perpetrated or experienced sexual violence, and shared applicable literature with other team members on the topic as logged in our meeting notes (e.g., [39, 49, 51, 52]). This was explicitly rooted in the trauma-informed principle of safety from its initial recommendation amongst the team because the utility of behaviorally-specific wording lies in avoiding phrases that may be perceived as blaming an individual for their experience or accusing them of engaging in harmful behavior.
As a result of this guidance Ube avoids use of words like "harm", "violence", and "consent". Donors are also never referred to as "victim" or "perpetrator" nor is the word "trauma" ever explicitly used. These words have heavy connotations - a donor who reads them in relation to their own data donation may either reflexively label their own experiences as sexual violence, or believe that researchers are labeling their experiences for them - thus usurping agency and biasing (if not overriding) data contextualization practices. For instance, instead of asking a data donor if they were the victim of sexual violence we ask "When sexual contact was attempted, did you want to engage in sexual contact?" Answers to this contextualization question would help us, as designers and developers, label the experience as sexual violence (if the answer is no) while avoiding the phrase itself and the emotional and psychological predispositions that come with it.
5.2.2 Use data contextualization as an opportunity to acknowledge the complexity and uncertainty in data being donated. The process of discovering a potential sexual partner through a dating app and then meeting them face-to-face for a sexual encounter can involve many steps over multiple online platforms and face-to-face meetings. Because this process can span days, there is ample opportunity for individuals to collect various and conflicting signals of sexual interest, and also modify their own feelings and willingness to engage in sex. Pursuant to trauma-informed principle #5 (empowerment, voice, and choice), a design activity we engaged in during some cognitive walkthroughs was to reframe data contextualization as having a two-way purpose: to allow donors to provide explanatory context about a sexual experience, but also to acknowledge to the donors the complexity and uncertainty they may have felt during the experience. This involved extensive debates on how to word data donation and contextualization prompts that allow for donors to have changed their mind on willingness to have sex, and to potentially have had uncertain feelings in the moment that a sexual act occurred. Per one moment in a cognitive walkthrough that preceded debate on a particular data contextualization prompt: "There's a little bit of a discrepancy here because you're asking whether they wanted to have sexual contact when you met face to face, not when the act occurred. And they could change their mind from like the initial meeting to later when it's actually occurring." This was followed by discussion of two different approaches to addressing the issue, such as editing the wording of that particular prompt or separating it into multiple prompts to inquire about desire for sexual contact at different points in time.
5.3 Design Goal 3: Realize and Respond to the Trauma of Data Donation
TIA assumptions adapted: Realize the effect of trauma; Respond to trauma. Review meetings of the initial Figma mockups for Ube regularly resulted in notes on the seemingly inevitable risk that using Ube could cause new trauma through contribution of, and reflection on, data pertaining to increasingly intimate details of sexual consent. We distinguish this from re-traumatization, which we sought to mitigate in design goal 2 with how donation and contextualization happens. Rather, here we refer to the realization that data donation of sexual experience, in and of itself, can be a traumatic experience. An outcome of the first two cognitive walkthroughs was the need to add elements to Ube’s design specifically for responding to, and helping users with, traumatization that may occur despite best efforts for mitigation. We mapped the ensuing design activities to trauma-informed principle #1 (safety) and #4 (collaboration & mutuality) because they revolved around inclusion of users in decision-making over their continued participation in donation and post-donation care. We describe two such activities below.
5.3.1 Incorporate assessment of donors’ well-being during their data donation journey. During cognitive walkthroughs, discussion sometimes veered into speculation over "how Ube can know when the data donation journey is too much" or in other words, the point to which a donor's mental well-being and comfort would necessitate a pause or stoppage of the data donation. This was most typically discussed after a particularly "heavy" prompt for data contextualization, such as inquiries into whether a donor was able to communicate that they wanted to stop a sexual act that they did not want. A decision from these cognitive walkthroughs was to intersperse "check-ins" that inquire about the donor's mental state during the data donation journey that determine if prompting should be discontinued. After broaching and discussing conceptual ideas verbally in team meetings following the first couple cognitive walkthroughs we concluded on check-ins that took the form of questions that Ube directly asks the user. Refer to Figure 3.
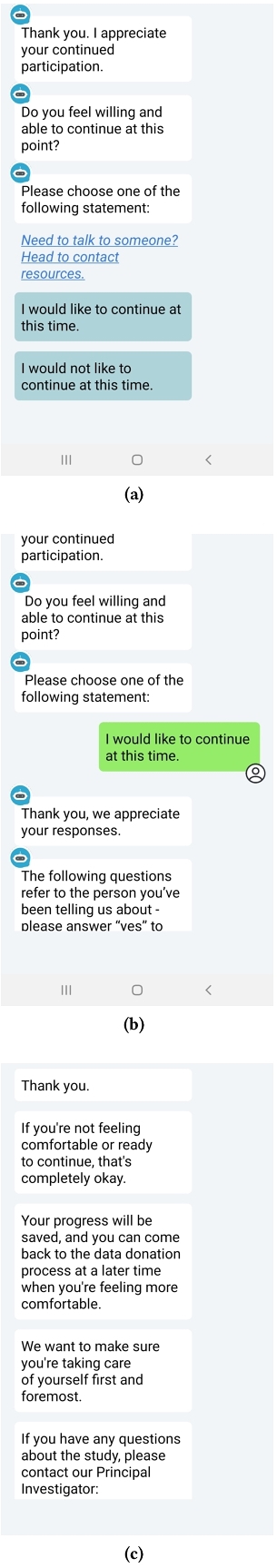
5.3.2 Curate trauma resources that data donors may need access to. We further incorporated the trauma-informed principle of peer support by curating a resource list that was uniquely applicable to our data donation context of sexual violence and which would be provided to users if they opted to discontinue data donation during a mental health check-in and also at the conclusion of any data donation journey. This curation was a collaborative exercise post-cognitive walkthroughs through which we used suggestions from NURSE1 and SHELTER1-2 as a starting point to reflect on which resources to provide and how to explain those resources in a way that does not risk labeling donors as necessarily "in need" of such resources. NURSE1 made the ultimate decision on resources and related interface designs.
We divided resources into two categories: sexual violence resources and mental health resources. Sexual violence resources include 911, the Rape, Abuse, and Incest National Network (RAINN), and contact information for NURSE1 who would not administer care services directly but serve as a connector to further/tailored resource recommendations if the user is confused by the default options or finds them unsatisfactory. Mental Health resources include the National Institute of Mental Health, the National Suicide Prevention Lifeline, and a 24/7 Crisis Text Line. Importantly, all of these resources include a short sentence describing the services they each provide. We should also note that this is the only place in Ube where the term "sexual violence" is explicitly used.
5.4 Design Goal 4: Maintain Donor Agency Over Donated Data
TIA assumptions adapted: Realize the effect of trauma; Resist re-traumatization. The effects of trauma can be wide-ranging, with a loss of control over one's emotions, body, and even recovery being common examples in the TIA literature shared amongst the team during and after meetings (e.g., [37]). Accordingly, the earliest interface mockups created and discussed for Ube were not actually prompts for data donation and contextualization, but rather iterative ideas for how to provide users autonomy over their data donations, including granular control over which data they donate and contextualize, and availability of the data to researchers or technology developers post-donation. We deemed pursuits towards donor agency to inherently align with the trauma-informed principles of empowerment, voice, & choice as well as trust & transparency. We describe two design activities pursuant to donor agency below.
5.4.1 Support donation of selectively chosen data rather than passive data dumps. Formative discussions about what UX1 described as Ube’s "design language" pertained to fundamental approaches to data donation, particularly passive versus active donation. Social platforms, including dating apps, often afford users the ability to download all of their usage data as a JSON file which could be easily uploaded to a data donation platform - this has been called passive data donation in prior literature [9] that UX1 shared and presented to the rest of the team. At first we planned to use passive data donation because leading dating apps like Bumble and Tinder afforded a JSON download option, however our team ultimately opted against this approach after discussions around the detrimental impact of "data dumps" on donor agency. There were concerns of re-traumatization through perceptually "forcing an online dater to donate all" of their usage data, including experiences they are not comfortable enough to disclose yet.
We accordingly designed for selective data donation through which a donor uploads only specific data that they are comfortable providing. This took the form of a screenshot uploading feature in which a donor uploads dating app profiles and messaging interactions as screenshots that would then be subjected to text extraction after the donation journey is completed. For example, Ube may prompt the donor with "Please upload screenshots of your messages with this person that expressed your disinterest in sexual contact."
We acknowledged in the design process the friction that selective data donation added to the user experience, but found this to be a necessary tradeoff for donor agency and trauma mitigation. We afforded additional capabilities for donors to modify or control donated data through automatic de-identification of personal details and manual censoring of particular parts of screenshots that the donor may feel uncomfortable sharing, such as the names of other users or particularly graphic portions of message exchanges. This is supported through a screenshot editing feature in which the donor can place "stickers" (i.e., small, opaque shapes they may place over any section of an image) over any part of a donated screenshot.
5.4.2 Scaffold interface design around donor choice. After drafting data donation/contextualization prompts (see Design Goal 1), the first set of interface design mockups focused on the homepage and menu placement during data donation journeys to foreground "donor choice" which team members primarily envisioned through demands for functionality to skip, edit, and delete data donations. We arrived at a homepage mockup that centered on the option to review and subsequently modify or delete prior donation sessions. Exercising the latter option in our completed Ube application completely deletes the donation from our servers, making it inaccessible and unrecoverable by researchers/platform operators. This was considered important functionality in team meetings because a donor's feelings on a particular sexual experience may change over time, which could lead to decisions to revoke access to the experience. Data agency controls were later added to a hamburger icon during data donation journeys, citing similar rationale.
6 DISCUSSION
In this paper we documented a trauma-informed design process for integrating the principles of the trauma-informed approach (TIA) into the design and development of Ube, a data donation platform for sexual experiences in online dating to improve sexual risk detection AI. To our understanding this is amongst the first works to unpack how the principles of TIA were incorporated into technology design. The practices within our trauma-informed design process evolved throughout Ube’s 12-month development cycle and were retrospectively organized with reflexive thematic analysis [18] into a coherent mapping of three procedural elements: design goals to translate TIA assumptions to the application domain, design activities mapping to trauma-informed principles, and consequent design decisions. Beyond simply recommending that future development teams follow our trauma-informed design process at project inception, we offer further methodological reflections that fall outside of our design documentation and thematic analysis.
Assign a "champion" to ensure TIA is correctly understood and applied. A concern of some team members during the design process, particularly those without a professional background in trauma, was superficial or incorrect integration of TIA - potentially resulting in a data donation platform that may be described as trauma-informed, but that would fail the expectations of practitioners in trauma-informed care. This concern usually manifested through requests to clarify nuances between the four assumptions and six principles of TIA, and later through challenges to interpretations and over-extrapolations of how specific design choices in Ube reflected trauma-informed principles. Looking back, having team members with professional experience in TIA was not only complimentary to expertise in UX design, online dating, and AI, but essential to proper adaptation of TIA. The TIA literature goes so far as to recommend having a team member serve as "champion" whose primary responsibility is to ensure proper adherence to TIA and make ultimate judgment calls over whether the principles are adhered to [45]. Given the risk of superficially applying TIA, we consider it mandatory that trauma-informed design teams have a champion, and that the role be fulfilled by someone with training in TIC or TIA - in our case it was NURSE1.
Involve trauma experts and care practitioners early in design to inform foundational design directions and minimize drastic design changes. A sexual assault nurse examiner (SANE) was involved in the design project from inception, yet it was not until month 7 that additional trauma experts (sexual and domestic violence shelter workers) were incorporated through cognitive walkthroughs of the Ube prototype. Dialogue between these experts lent itself to critical reflections of, and eventual revisions to, Ube’s design that were not previously as apparent in discussions with other team members proficient in areas of UX design, psychology, and online dating. This led to some significant additions and alterations to Ube’s design that ultimately delayed the development timeline. In retrospect we should have involved these additional trauma experts earlier to inform design directions at earlier stages before labor was put into interface design and development for aspects that would eventually change. An addendum to our previous recommendation is to involve trauma experts on the design team as early as possible to avoid drastic and time-consuming design direction changes.
Dedicate time to proxy knowledge sharing. Ahmadpour and colleagues recommend involvement of "proxies" in trauma-informed design [1], by which they mean stakeholders who are not target users, but individuals who have extensive experience interacting with the target users. A benefit of proxy involvement is the conscious limiting of re-traumatization risk caused through direct participation of people who have experienced trauma. Our experience completely aligns with this recommendation. Our team members in nursing and public health have collectively interacted with an extensive number of people who have experienced sexual violence, and their involvement served as a vector for all of those experiences. Yet while their experiences with primary stakeholders were occasionally expressed in their explanations for decisions and reactions to Ube’s design, in retrospect we should have dedicated time specifically for our proxy members to share their experiences with primary stakeholders. This is especially true for the domestic and sexual violence shelters workers who entered the design process at the cognitive walkthrough stage where they had relatively little time to elaborate on their professional experience and provide deeper understanding of primary stakeholders. The providing of this deeper understanding of target stakeholders aligns with guidelines in CHI literature for proxy involvement [1, 28]. It would be particularly effective in trauma-informed design because the relaying of professional experience as vectors to target users can foster proactive articulation of design goals, and activities and interface choices rooted in those experiences, rather than reactive guidance to already-created prototypes.
Treat assessment of comparable applications as an early trauma-informed design activity. As noted in the Method section, UX1 had reviewed existing data donation platforms in the literature (e.g., [40, 75]) early in our design process as a way to familiarize all team members with the state of the application domain. It was not until much later in design, when a prototype of Ube was fully developed and we were preparing to write this paper, that we revisited prior data donation platform designs to reflect on the possible consequences of our trauma-informed design goals and activities on Ube’s design choices that contrast with said platforms. Notably, our choice to design for "active" [9], selective data donation rooted in the trauma-informed principle of empowerment, voice, & choice deviates starkly from the predominantly passive data donation designs in other platforms [41, 74] (e.g., uploading a JSON file that indiscriminately contains all of the user's data). Another is our use of behaviorally specific wording in data contextualization prompts - reflective of the trauma-informed principle of safety - instead of explicit reference to sexual violence and related terminology that necessitates a data donor to self-identify an experience as harm [3, 5]. We do not mean to assert that prior data donation platforms have been designed incorrectly, but rather that reflections on design choices in related applications can help clarify (potentially latent) trauma-informed design goals to guide the development of one's own technology. If we could re-do our design process we would review prior data donation platforms not just for familiarity, but as a basis for consciously honing our design goals mapped to TIA assumptions - for example, by expounding on why we think design choices evidenced in other applications would work (or not) in Ube according to TIA.
Develop structures to address traumatization of the design team. While we drew from TIA to seek mitigation of re-traumatization of data donors, we must also note the potential for this project to be (re-)traumatizing to the designers and developers of our data donation platform. TIA literature does encourage the creation of structures and procedures to mitigate re-traumatization amongst team members [45], but this was not explicitly considered amongst our team. During reflection we concluded that this was most likely due to the the presumption that we individually had already developed personal coping mechanisms through our prior sexual violence work, yet this is clearly flawed thinking given the fact that prior experience in this space does not render any of us immune to future effects on our well-being. We acknowledge that deliberate reflections on discomfort associated with design of Ube over an extended period would have benefited our team. Such discussions are being foregrounded in preparations for public release of our data donation platform with dating app users.
7 CONCLUSION
In recent years there has been consideration of how to formally integrate trauma into technology design processes, leading to frameworks and guidelines for adapting the trauma-informed approach (TIA) from public health and social work to HCI. The area of trauma-informed computing is still in formative stages with scarce public discourse on how design teams apply TIA and qualify the resultant technology as adhering to trauma-informed principles. We address this by reporting on a 12-month development cycle to produce Ube, a data donation platform for collecting online dating sexual consent data to improve sexual risk detection AI. Through thematic analysis of design documentation we elucidate an evolving trauma-informed design process that determined our integration of TIA into Ube’s design, comprising three key elements: 1) design goals that reflect the team's agreement over what it would mean for the resultant technology to satisfy the core assumptions of TIA; 2) design activities reflective of specific trauma-informed principles; and 3) design choices culminating from such activities. We offer methodological recommendations for future practice of trauma-informed design.
ACKNOWLEDGMENTS
This work is partially supported by the U.S. National Science Foundation under Grant No. IIS-2211896 and Grant No. IIS-2211897.
REFERENCES
- Naseem Ahmadpour, Lian Loke, Carl Gray, Yidan Cao, Chloe Macdonald, and Rebecca Hart. 2023. Understanding how technology can support social-emotional learning of children: a dyadic trauma-informed participatory design with proxies. In Proceedings of the 2023 CHI Conference on Human Factors in Computing Systems. ACM, Hamburg Germany, 1–17. https://doi.org/10.1145/3544548.3581032
- Alex A. Ahmed, Teresa Almeida, Judeth Oden Choi, Jon Pincus, and Kelly Ireland. 2018. What's at Issue: Sex, Stigma, and Politics in ACM Publishing. In Extended Abstracts of the 2018 CHI Conference on Human Factors in Computing Systems. ACM, Montreal QC Canada, 1–10. https://doi.org/10.1145/3170427.3188400
- Shiza Ali, Afsaneh Razi, Seunghyun Kim, Ashwaq Alsoubai, Joshua Gracie, Munmun De Choudhury, Pamela J. Wisniewski, and Gianluca Stringhini. 2022. Understanding the Digital Lives of Youth: Analyzing Media Shared within Safe Versus Unsafe Private Conversations on Instagram. In CHI Conference on Human Factors in Computing Systems. ACM, New Orleans LA USA, 1–14. https://doi.org/10.1145/3491102.3501969
- Hanan Khalid Aljasim and Douglas Zytko. 2022. Foregrounding Women's Safety in Mobile Social Matching and Dating Apps: A Participatory Design Study. Proc. ACM Hum.-Comput. Interact. 7, GROUP, Article 9 (dec 2022), 25 pages. https://doi.org/10.1145/3567559
- Ashwaq Alsoubai, Xavier V. Caddle, Ryan Doherty, Alexandra Taylor Koehler, Estefania Sanchez, Munmun De Choudhury, and Pamela J. Wisniewski. 2022. MOSafely, Is that Sus? A Youth-Centric Online Risk Assessment Dashboard. In Companion Computer Supported Cooperative Work and Social Computing. ACM, Virtual Event Taiwan, 197–200. https://doi.org/10.1145/3500868.3559710
- Nazanin Andalibi and Andrea Forte. 2018. Announcing Pregnancy Loss on Facebook: A Decision-Making Framework for Stigmatized Disclosures on Identified Social Network Sites. In Proceedings of the 2018 CHI Conference on Human Factors in Computing Systems(CHI ’18). Association for Computing Machinery, New York, NY, USA, 1–14. https://doi.org/10.1145/3173574.3173732
- Nazanin Andalibi, Oliver L. Haimson, Munmun De Choudhury, and Andrea Forte. 2016. Understanding Social Media Disclosures of Sexual Abuse Through the Lenses of Support Seeking and Anonymity. In Proceedings of the 2016 CHI Conference on Human Factors in Computing Systems. ACM, San Jose California USA, 3906–3918. https://doi.org/10.1145/2858036.2858096
- Karla Badillo-Urquiola, Carl Antoine, Amanda Nisenbaum, Zachary Daniel Shea, and Pamela J. Wisniewski. 2022. “30 Days:” An EMA Diary Mobile App & Web Tool. In CHI Conference on Human Factors in Computing Systems Extended Abstracts. ACM, New Orleans LA USA, 1–5. https://doi.org/10.1145/3491101.3519888
- Karla Badillo-Urquiola, Zachary Shea, Zainab Agha, Irina Lediaeva, and Pamela Wisniewski. 2021. Conducting Risky Research with Teens: Co-designing for the Ethical Treatment and Protection of Adolescents. Proceedings of the ACM on Human-Computer Interaction 4, CSCW3 (Jan 2021), 1–46. https://doi.org/10.1145/3432930
- Karla Badillo-Urquiola, Zachary Shea, Zainab Agha, Irina Lediaeva, and Pamela Wisniewski. 2021. Conducting Risky Research with Teens: Co-designing for the Ethical Treatment and Protection of Adolescents. Proceedings of the ACM on Human-Computer Interaction 4, CSCW3 (Jan 2021), 1–46. https://doi.org/10.1145/3432930
- Jeffrey Bardzell, Shaowen Bardzell, Peter Dalsgaard, Shad Gross, and Kim Halskov. 2016. Documenting the Research Through Design Process. In Proceedings of the 2016 ACM Conference on Designing Interactive Systems. ACM, Brisbane QLD Australia, 96–107. https://doi.org/10.1145/2901790.2901859
- Catherine Barwulor, Allison McDonald, Eszter Hargittai, and Elissa M. Redmiles. 2021. “Disadvantaged in the American-dominated Internet”: Sex, Work, and Technology. In Proceedings of the 2021 CHI Conference on Human Factors in Computing Systems. ACM, Yokohama Japan, 1–16. https://doi.org/10.1145/3411764.3445378
- Matthew Bietz, Kevin Patrick, and Cinnamon Bloss. 2019. Data Donation as a Model for Citizen Science Health Research. Citizen Science: Theory and Practice 4, 1 (Mar 2019), 6. https://doi.org/10.5334/cstp.178
- Andrea Blanch, Beth Filson, Darby Penney, and Cathy Cave. 2012. Engaging women in trauma-informed peer support: A guidebook. Alexandria, VA: National Center for Trauma-Informed Care (2012).
- Anja Botha and Henriëtte van den Berg. 2016. Trauma exposure and life satisfaction among at-risk black South African adolescents. Journal of Psychology in Africa 26, 6 (2016), 500–507.
- Robert Bowman, Camille Nadal, Kellie Morrissey, Anja Thieme, and Gavin Doherty. 2023. Using Thematic Analysis in Healthcare HCI at CHI: A Scoping Review. In Proceedings of the 2023 CHI Conference on Human Factors in Computing Systems (<conf-loc>, <city>Hamburg</city>, <country>Germany</country>, </conf-loc>) (CHI ’23). Association for Computing Machinery, New York, NY, USA, Article 491, 18 pages. https://doi.org/10.1145/3544548.3581203
- Patrick E. Boyle and Christina M. Delos Reyes. 2015. Trauma-Informed Care: Core Principle #2, Trustworthiness and Transparency. url: https://case.edu/socialwork/centerforebp/sites/case.edu.centerforebp/files/2021-03/2015-0218_TICforRPHVideoconference.pdf.
- Virginia Braun and Victoria Clarke. 2021. Thematic Analysis: A Practical Guide. (2021), 1–376.
- Virginia Braun, Victoria Clarke, Nikki Hayfield, and Gareth Terry. 2019. Thematic Analysis. Springer Singapore, Singapore, 843–860. https://doi.org/10.1007/978-981-10-5251-4_103
- Paul Bucci, David Marino, and Ivan Beschastnikh. 2023. Affective Robots Need Therapy. ACM Transactions on Human-Robot Interaction 12, 2 (Jun 2023), 1–22. https://doi.org/10.1145/3543514
- Bumble. [n. d.]. Bumble Buzz ([n. d.]). https://bumble.com/en-us/the-buzz/bumble-open-source-private-detector-ai-cyberflashing-dick-pics Accessed: December 11 2023.
- Melissa Burkett and Karine Hamilton. 2012. Postfeminist sexual agency: Young women's negotiations of sexual consent. Sexualities 15, 7 (Oct 2012), 815–833. https://doi.org/10.1177/1363460712454076
- Elie Bursztein, Einat Clarke, Michelle DeLaune, David M. Elifff, Nick Hsu, Lindsey Olson, John Shehan, Madhukar Thakur, Kurt Thomas, and Travis Bright. 2019. Rethinking the Detection of Child Sexual Abuse Imagery on the Internet. In The World Wide Web Conference. ACM, San Francisco CA USA, 2601–2607. https://doi.org/10.1145/3308558.3313482
- Janet X. Chen, Allison McDonald, Yixin Zou, Emily Tseng, Kevin A Roundy, Acar Tamersoy, Florian Schaub, Thomas Ristenpart, and Nicola Dell. 2022. Trauma-Informed Computing: Towards Safer Technology Experiences for All. In CHI Conference on Human Factors in Computing Systems. ACM, New Orleans LA USA, 1–20. https://doi.org/10.1145/3491102.3517475
- Edmond Pui Hang Choi, Janet Yuen Ha Wong, and Daniel Yee Tak Fong. 2018. An Emerging Risk Factor of Sexual Abuse: The Use of Smartphone Dating Applications. Sexual Abuse 30, 4 (Jun 2018), 343–366. https://doi.org/10.1177/1079063216672168
- cms user27. [n. d.]. More under 20s sexually assaulted after meeting offenders on dating sites. https://www.nationalcrimeagency.gov.uk/news/more-under-20s-sexually-assaulted-after-meeting-offenders-on-dating-sites
- Alan Cooper, Robert Reimann, Dave Cronin, and Alan Cooper. 2014. About face: the essentials of interaction design (fourth edition ed.). John Wiley and Sons, Indianapolis, IN.
- Jiamin Dai and Karyn Moffatt. 2021. Surfacing the Voices of People with Dementia: Strategies for Effective Inclusion of Proxy Stakeholders in Qualitative Research. In Proceedings of the 2021 CHI Conference on Human Factors in Computing Systems (<conf-loc>, <city>Yokohama</city>, <country>Japan</country>, </conf-loc>) (CHI ’21). Association for Computing Machinery, New York, NY, USA, Article 374, 13 pages. https://doi.org/10.1145/3411764.3445756
- Stephanie J Dallam. 2010. A model of the retraumatization process: A meta-synthesis of childhood sexual abuse survivors’ experiences in healthcare. Ph. D. Dissertation. University of Kansas.
- Isha Datey, Hanan Khalid Aljasim, and Douglas Zytko. 2022. Repurposing AI in Dating Apps to Augment Women's Strategies for Assessing Risk of Harm. In Companion Publication of the 2022 Conference on Computer Supported Cooperative Work and Social Computing (Virtual Event, Taiwan) (CSCW’22 Companion). Association for Computing Machinery, New York, NY, USA, 150–154. https://doi.org/10.1145/3500868.3559472
- Prema Dev, Jessica Medina, Zainab Agha, Munmun De Choudhury, Afsaneh Razi, and Pamela J. Wisniewski. 2022. From Ignoring Strangers’ Solicitations to Mutual Sexting with Friends: Understanding Youth's Online Sexual Risks in Instagram Private Conversations. In Companion Computer Supported Cooperative Work and Social Computing. ACM, Virtual Event Taiwan, 94–97. https://doi.org/10.1145/3500868.3559469
- Daniel Diethei, Jasmin Niess, Carolin Stellmacher, Evropi Stefanidi, and Johannes Schöning. 2021. Sharing Heartbeats: Motivations of Citizen Scientists in Times of Crises. In Proceedings of the 2021 CHI Conference on Human Factors in Computing Systems. ACM, Yokohama Japan, 1–15. https://doi.org/10.1145/3411764.3445665
- Kari N. Duerksen and Erica M. Woodin. 2019. Technological intimate partner violence: Exploring technology-related perpetration factors and overlap with in-person intimate partner violence. Computers in Human Behavior 98 (Sep 2019), 223–231. https://doi.org/10.1016/j.chb.2019.05.001
- Catherine D'Ignazio, Rebecca Michelson, Alexis Hope, Josephine Hoy, Jennifer Roberts, and Kate Krontiris. 2020. “The Personal is Political”: Hackathons as Feminist Consciousness Raising. Proceedings of the ACM on Human-Computer Interaction 4, CSCW2 (Oct 2020), 1–23. https://doi.org/10.1145/3415221
- Denise E. Elliott, Paula Bjelajac, Roger D. Fallot, Laurie S. Markoff, and Beth Glover Reed. 2005. Trauma-informed or trauma-denied: Principles and implementation of trauma-informed services for women. Journal of Community Psychology 33, 4 (2005), 461–477. https://doi.org/10.1002/jcop.20063 arXiv:https://onlinelibrary.wiley.com/doi/pdf/10.1002/jcop.20063
- Sheena Erete, Yolanda A. Rankin, and Jakita O. Thomas. 2021. I Can't Breathe: Reflections from Black Women in CSCW and HCI. Proceedings of the ACM on Human-Computer Interaction 4, CSCW3 (Jan 2021), 1–23. https://doi.org/10.1145/3432933
- Center for Substance Abuse Treatment et al. 2014. Trauma-informed care in behavioral health services. (2014).
- Diana Freed, Jackeline Palmer, Diana Elizabeth Minchala, Karen Levy, Thomas Ristenpart, and Nicola Dell. 2017. Digital Technologies and Intimate Partner Violence: A Qualitative Analysis with Multiple Stakeholders. Proceedings of the ACM on Human-Computer Interaction 1, CSCW (Dec 2017), 1–22. https://doi.org/10.1145/3134681
- Daniel J. Gildner, Mitchell Kirwan, Scott M. Pickett, and Michele R. Parkhill. 2021. Impulse Control Difficulties and Hostility Toward Women as Predictors of Relationship Violence Perpetration in an Undergraduate Male Sample. Journal of Interpersonal Violence 36, 9–10 (May 2021), NP4653–4678. https://doi.org/10.1177/0886260518792972
- Alejandra Gomez Ortega, Jacky Bourgeois, and Gerd Kortuem. 2022. Reconstructing Intimate Contexts through Data Donation: A Case Study in Menstrual Tracking Technologies. In Nordic Human-Computer Interaction Conference (Aarhus, Denmark) (NordiCHI ’22). Association for Computing Machinery, New York, NY, USA, Article 8, 12 pages. https://doi.org/10.1145/3546155.3546646
- Alejandra Gómez Ortega, Jacky Bourgeois, and Gerd Kortuem. 2023. What is Sensitive About (Sensitive) Data? Characterizing Sensitivity and Intimacy with Google Assistant Users. In Proceedings of the 2023 CHI Conference on Human Factors in Computing Systems. ACM, Hamburg Germany, 1–16. https://doi.org/10.1145/3544548.3581164
- Ian Harris, Alan Tien Thanh Dao, Jane Young, Michael Solomon, Bin Badrudin Jalaludin, and Hamish Rae. 2007. Factors predicting patient satisfaction following major trauma. Injury 38, 9 (2007), 1102–1108.
- Jennifer S. Hirsch, Shamus R. Khan, Alexander Wamboldt, and Claude A. Mellins. 2019. Social Dimensions of Sexual Consent Among Cisgender Heterosexual College Students: Insights From Ethnographic Research. Journal of Adolescent Health 64, 1 (Jan 2019), 26–35. https://doi.org/10.1016/j.jadohealth.2018.06.011
- Tad Hirsch. 2020. Practicing Without a License: Design Research as Psychotherapy. In Proceedings of the 2020 CHI Conference on Human Factors in Computing Systems(CHI ’20). Association for Computing Machinery, New York, NY, USA, 1–11. https://doi.org/10.1145/3313831.3376750
- Larke N Huang, Rebecca Flatow, Tenly Biggs, Sara Afayee, Kelley Smith, Thomas Clark, and Mary Blake. 2014. SAMHSA's Concept of Truama and Guidance for a Trauma-Informed Approach. (2014).
- Jina Huh-Yoo, Afsaneh Razi, Diep N. Nguyen, Sampada Regmi, and Pamela J. Wisniewski. 2023. “Help Me:” Examining Youth's Private Pleas for Support and the Responses Received from Peers via Instagram Direct Messages. In Proceedings of the 2023 CHI Conference on Human Factors in Computing Systems. ACM, Hamburg Germany, 1–14. https://doi.org/10.1145/3544548.3581233
- Shannon Kelly, Benjamin Lauren, and Kaitlyn Nguyen. 2021. Trauma-informed Web Heuristics for Communication Designers. In The 39th ACM International Conference on Design of Communication. ACM, Virtual Event USA, 172–176. https://doi.org/10.1145/3472714.3473638
- Seunghyun Kim, Afsaneh Razi, Gianluca Stringhini, Pamela J. Wisniewski, and Munmun De Choudhury. 2021. A Human-Centered Systematic Literature Review of Cyberbullying Detection Algorithms. Proceedings of the ACM on Human-Computer Interaction 5, CSCW2 (Oct 2021), 1–34. https://doi.org/10.1145/3476066
- Mitchell Kirwan, Michele R. Parkhill, Blake A. Schuetz, and Ashley Cox. 2019. A Within-Subjects Analysis of Men's Alcohol-Involved and Nonalcohol-Involved Sexual Assaults. Journal of Interpersonal Violence 34, 16 (Aug 2019), 3392–3413. https://doi.org/10.1177/0886260516670179
- Rolf J Kleber. 2019. Trauma and public mental health: A focused review. Frontiers in psychiatry 10 (2019), 451.
- Mary P. Koss, Antonia Abbey, Rebecca Campbell, Sarah Cook, Jeanette Norris, Maria Testa, Sarah Ullman, Carolyn West, and Jacquelyn White. 2007. Revising the SES: A Collaborative Process to Improve Assessment of Sexual Aggression and Victimization. Psychology of Women Quarterly 31, 4 (Dec 2007), 357–370. https://doi.org/10.1111/j.1471-6402.2007.00385.x
- Mary P. Koss, Kevin M. Swartout, Elise C. Lopez, Raina V. Lamade, Elizabeth J. Anderson, Carolyn L. Brennan, and Robert A. Prentky. 2022. The Scope of Rape Victimization and Perpetration Among National Samples of College Students Across 30 years. Journal of Interpersonal Violence 37, 1–2 (Jan 2022), NP25–NP47. https://doi.org/10.1177/08862605211050103
- David Leimstädtner, Peter Sörries, and Claudia Müller-Birn. 2022. Unfolding Values through Systematic Guidance: Conducting a Value-Centered Participatory Workshop for a Patient-Oriented Data Donation. In Mensch und Computer 2022. ACM, Darmstadt Germany, 477–482. https://doi.org/10.1145/3543758.3547560
- Roxanne Leitão. 2018. Digital Technologies and their Role in Intimate Partner Violence. In Extended Abstracts of the 2018 CHI Conference on Human Factors in Computing Systems. ACM, Montreal QC Canada, 1–6. https://doi.org/10.1145/3170427.3180305
- Jill Levenson. 2017. Trauma-Informed Social Work Practice. Social Work 62, 2 (01 2017), 105–113. https://doi.org/10.1093/sw/swx001 arXiv:https://academic.oup.com/sw/article-pdf/62/2/105/11036796/swx001.pdf
- Lian Loke, Aaron Blishen, Carl Gray, and Naseem Ahmadpour. 2021. Safety, Connection and Reflection: Designing with Therapists for Children with Serious Emotional Behaviour Issues. In Proceedings of the 2021 CHI Conference on Human Factors in Computing Systems. ACM, Yokohama Japan, 1–17. https://doi.org/10.1145/3411764.3445178
- Cristina M López, Arthur R Andrews III, Andrea M Chisolm, Michael A De Arellano, Benjamin Saunders, Dean Kilpatrick, et al. 2017. Racial/ethnic differences in trauma exposure and mental health disorders in adolescents.Cultural diversity and ethnic minority psychology 23, 3 (2017), 382.
- Donna Maguire and James Taylor. 2019. A Systematic Review on Implementing Education and Training on Trauma-Informed Care to Nurses in Forensic Mental Health Settings. Journal of Forensic Nursing 15, 4 (Oct 2019), 242–249. https://doi.org/10.1097/JFN.0000000000000262
- Benjamin Maus, Dario Salvi, and Carl Magnus Olsson. 2020. Enhancing citizens trust in technologies for data donation in clinical research: validation of a design prototype. In 10th International Conference on the Internet of Things Companion. ACM, Malmö Sweden, 1–8. https://doi.org/10.1145/3423423.3423430
- Shery Mead. 2014. Intentional peer support: An alternative approach. Intentional Peer Support West Chesterfield.
- Yuval Neria, Evelyn Bromet, Sylvia Sievers, Janet Lavelle, and Laura Fochtmann. 2002. Trauma exposure and posttraumatic stress disorder in psychosis: Findings from a first-admission cohort. Journal of consulting and clinical psychology 70 (Mar 2002), 246–51. https://doi.org/10.1037//0022-006X.70.1.246
- Ihudiya Finda Ogbonnaya-Ogburu, Angela D.R. Smith, Alexandra To, and Kentaro Toyama. 2020. Critical Race Theory for HCI. In Proceedings of the 2020 CHI Conference on Human Factors in Computing Systems. ACM, Honolulu HI USA, 1–16. https://doi.org/10.1145/3313831.3376392
- Ihudiya Finda Ogbonnaya-Ogburu, Kentaro Toyama, and Tawanna Dillahunt. 2018. Returning Citizens’ Job Search and Technology Use: Preliminary Findings. In Companion of the 2018 ACM Conference on Computer Supported Cooperative Work and Social Computing. ACM, Jersey City NJ USA, 365–368. https://doi.org/10.1145/3272973.3274098
- Jakob Ohme, Theo Araujo, Claes H. de Vreese, and Jessica Taylor Piotrowski. 2021. Mobile data donations: Assessing self-report accuracy and sample biases with the iOS Screen Time function. Mobile Media & Communication 9, 2 (May 2021), 293–313. https://doi.org/10.1177/2050157920959106
- Resmiye Oral, Carol Coohey, Kasra Zarei, Aislinn Conrad, Anne Nielsen, Lucy Wibbenmeyer, Rachel Segal, Armeda Stevenson Wojciak, Charles Jennissen, and Corinne Peek-Asa. 2020. Nationwide efforts for trauma-informed care implementation and workforce development in healthcare and related fields: a systematic review. The Turkish journal of pediatrics 62, 6 (2020), 906–920. https://doi.org/10.24953/turkjped.2020.06.002
- Kentrell Owens, Camille Cobb, and Lorrie Cranor. 2021. “You Gotta Watch What You Say”: Surveillance of Communication with Incarcerated People. In Proceedings of the 2021 CHI Conference on Human Factors in Computing Systems. ACM, Yokohama Japan, 1–18. https://doi.org/10.1145/3411764.3445055
- Hyanghee Park and Joonhwan Lee. 2021. Designing a Conversational Agent for Sexual Assault Survivors: Defining Burden of Self-Disclosure and Envisioning Survivor-Centered Solutions. In Proceedings of the 2021 CHI Conference on Human Factors in Computing Systems. ACM, Yokohama Japan, 1–17. https://doi.org/10.1145/3411764.3445133
- Tomaszewska Paulina and Schuster Isabell. 2020. Comparing Sexuality-Related Cognitions, Sexual Behavior, and Acceptance of Sexual Coercion in Dating App Users and Non-Users. Sexuality Research & Social Policy 17, 2 (Jun 2020), 188–198. https://doi.org/10.1007/s13178-019-00397-x
- Eric R Pedersen, Layla Parast, Grant N Marshall, Terry L Schell, and Clayton Neighbors. 2017. A randomized controlled trial of a web-based, personalized normative feedback alcohol intervention for young-adult veterans.Journal of consulting and clinical psychology 85, 5 (2017), 459.
- Anastasia Powell and Nicola Henry. 2019. Technology-Facilitated Sexual Violence Victimization: Results From an Online Survey of Australian Adults. Journal of Interpersonal Violence 34, 17 (Sep 2019), 3637–3665. https://doi.org/10.1177/0886260516672055
- Hawra Rabaan and Lynn Dombrowski. 2023. Survivor-Centered Transformative Justice: An Approach to Designing Alongside Domestic Violence Stakeholders in US Muslim Communities. In Proceedings of the 2023 CHI Conference on Human Factors in Computing Systems(CHI ’23). Association for Computing Machinery, New York, NY, USA, 1–19. https://doi.org/10.1145/3544548.3580648
- Anjana Rajan, Lucy Qin, David W. Archer, Dan Boneh, Tancrede Lepoint, and Mayank Varia. 2018. Callisto: A Cryptographic Approach to Detecting Serial Perpetrators of Sexual Misconduct. In Proceedings of the 1st ACM SIGCAS Conference on Computing and Sustainable Societies. ACM, Menlo Park and San Jose CA USA, 1–4. https://doi.org/10.1145/3209811.3212699
- Casey Randazzo and Tawfiq Ammari. 2023. “If Someone Downvoted My Posts—That'd Be the End of the World”: Designing Safer Online Spaces for Trauma Survivors. In Proceedings of the 2023 CHI Conference on Human Factors in Computing Systems. ACM, Hamburg Germany, 1–18. https://doi.org/10.1145/3544548.3581453
- Afsaneh Razi, Ashwaq AlSoubai, Seunghyun Kim, Nurun Naher, Shiza Ali, Gianluca Stringhini, Munmun De Choudhury, and Pamela J Wisniewski. 2022. Instagram Data Donation: A Case Study on Collecting Ecologically Valid Social Media Data for the Purpose of Adolescent Online Risk Detection. (2022), 9.
- Afsaneh Razi, Ashwaq Alsoubai, Seunghyun Kim, Nurun Naher, Shiza Ali, Gianluca Stringhini, Munmun De Choudhury, and Pamela J. Wisniewski. 2022. Instagram Data Donation: A Case Study on Collecting Ecologically Valid Social Media Data for the Purpose of Adolescent Online Risk Detection. In Extended Abstracts of the 2022 CHI Conference on Human Factors in Computing Systems (New Orleans, LA, USA) (CHI EA ’22). Association for Computing Machinery, New York, NY, USA, Article 39, 9 pages. https://doi.org/10.1145/3491101.3503569
- Afsaneh Razi, Karla Badillo-Urquiola, and Pamela J. Wisniewski. 2020. Let's Talk about Sext: How Adolescents Seek Support and Advice about Their Online Sexual Experiences. In Proceedings of the 2020 CHI Conference on Human Factors in Computing Systems. ACM, Honolulu HI USA, 1–13. https://doi.org/10.1145/3313831.3376400
- Afsaneh Razi, Seunghyun Kim, Ashwaq Alsoubai, Gianluca Stringhini, Thamar Solorio, Munmun De Choudhury, and Pamela J. Wisniewski. 2021. A Human-Centered Systematic Literature Review of the Computational Approaches for Online Sexual Risk Detection. Proceedings of the ACM on Human-Computer Interaction 5, CSCW2 (Oct 2021), 1–38. https://doi.org/10.1145/3479609
- Peter Rhee, Bellal Joseph, Viraj Pandit, Hassan Aziz, Gary Vercruysse, Narong Kulvatunyou, and Randall S Friese. 2014. Increasing trauma deaths in the United States. Annals of surgery 260, 1 (2014), 13–21.
- Janine Rowse, Caroline Bolt, and Sanjeev Gaya. 2020. Swipe right: the emergence of dating-app facilitated sexual assault. A descriptive retrospective audit of forensic examination caseload in an Australian metropolitan service. Forensic Science, Medicine and Pathology 16, 1 (Mar 2020), 71–77. https://doi.org/10.1007/s12024-019-00201-7
- Coleen Sallot. 2021. Utilizing Virtual Play to Help Adopted Children with Trauma. In Extended Abstracts of the 2021 Annual Symposium on Computer-Human Interaction in Play(CHI PLAY ’21). Association for Computing Machinery, New York, NY, USA, 49–54. https://doi.org/10.1145/3450337.3483471
- Nithya Sambasivan, Julie Weber, and Edward Cutrell. 2011. Designing a phone broadcasting system for urban sex workers in India. In Proceedings of the SIGCHI Conference on Human Factors in Computing Systems(CHI ’11). Association for Computing Machinery, New York, NY, USA, 267–276. https://doi.org/10.1145/1978942.1978980
- SAMHSA. 2021. SAMHSA/ TIC Curriculum Instructor's Guidance., 72–73 pages. https://www.nasmhpd.org/sites/default/files/TraumaTIACurriculumTrainersManual_6-2-21.pdf Accessed: December 12 2023 [Online]..
- Devansh Saxena, Karla Badillo-Urquiola, Pamela Wisniewski, and Shion Guha. 2020. Child Welfare System: Interaction of Policy, Practice and Algorithms. In Companion of the 2020 ACM International Conference on Supporting Group Work. ACM, Sanibel Island Florida USA, 119–122. https://doi.org/10.1145/3323994.3369888
- Carol F Scott, Gabriela Marcu, Riana Elyse Anderson, Mark W Newman, and Sarita Schoenebeck. 2023. Trauma-Informed Social Media: Towards Solutions for Reducing and Healing Online Harm. In Proceedings of the 2023 CHI Conference on Human Factors in Computing Systems. ACM, Hamburg Germany, 1–20. https://doi.org/10.1145/3544548.3581512
- David M Shaw, Juliane V Gross, and Thomas C Erren. 2016. Data donation after death. EMBO reports 17, 1 (Jan 2016), 14–17. https://doi.org/10.15252/embr.201541802
- Anya Skatova and James Goulding. 2019. Psychology of personal data donation. PLOS ONE 14, 11 (Nov 2019), e0224240. https://doi.org/10.1371/journal.pone.0224240
- Rick Spencer. 2000. The streamlined cognitive walkthrough method, working around social constraints encountered in a software development company. In Proceedings of the SIGCHI conference on Human Factors in Computing Systems. ACM, The Hague The Netherlands, 353–359. https://doi.org/10.1145/332040.332456
- Angelika Strohmayer, Jenn Clamen, and Mary Laing. 2019. Technologies for Social Justice: Lessons from Sex Workers on the Front Lines. In Proceedings of the 2019 CHI Conference on Human Factors in Computing Systems. ACM, Glasgow Scotland Uk, 1–14. https://doi.org/10.1145/3290605.3300882
- Veronika Strotbaum, Monika Pobiruchin, Björn Schreiweis, Martin Wiesner, and Brigitte Strahwald. 2019. Your data is gold – Data donation for better healthcare?it - Information Technology 61, 5–6 (Oct 2019), 219–229. https://doi.org/10.1515/itit-2019-0024
- Sharifa Sultana, Mitrasree Deb, Ananya Bhattacharjee, Shaid Hasan, S.M.Raihanul Alam, Trishna Chakraborty, Prianka Roy, Samira Fairuz Ahmed, Aparna Moitra, M Ashraful Amin, A.K.M. Najmul Islam, and Syed Ishtiaque Ahmed. 2021. ‘Unmochon’: A Tool to Combat Online Sexual Harassment over Facebook Messenger. In Proceedings of the 2021 CHI Conference on Human Factors in Computing Systems. ACM, Yokohama Japan, 1–18. https://doi.org/10.1145/3411764.3445154
- Tinder. 2021. Tinder Newsroom (May 2021). https://www.tinderpressroom.com/2021-05-20-Tinder-Introduces-Are-You-Sure-, -an-Industry-First-Feature-That-is-Stopping-Harassment-Before-It-Starts Accessed: December 11 2023.
- Alexandra To, Angela D. R. Smith, Dilruba Showkat, Adinawa Adjagbodjou, and Christina Harrington. 2023. Flourishing in the Everyday: Moving Beyond Damage-Centered Design in HCI for BIPOC Communities. In Proceedings of the 2023 ACM Designing Interactive Systems Conference(DIS ’23). Association for Computing Machinery, New York, NY, USA, 917–933. https://doi.org/10.1145/3563657.3596057
- Alexandra To, Wenxia Sweeney, Jessica Hammer, and Geoff Kaufman. 2020. “They Just Don't Get It”: Towards Social Technologies for Coping with Interpersonal Racism. Proceedings of the ACM on Human-Computer Interaction 4, CSCW1 (May 2020), 1–29. https://doi.org/10.1145/3392828
- Kelli N Triplett, Richard G Tedeschi, Arnie Cann, Lawrence G Calhoun, and Charlie L Reeve. 2012. Posttraumatic growth, meaning in life, and life satisfaction in response to trauma.Psychological trauma: Theory, research, practice, and policy 4, 4 (2012), 400.
- Emily Tseng, Mehrnaz Sabet, Rosanna Bellini, Harkiran Kaur Sodhi, Thomas Ristenpart, and Nicola Dell. 2022. Care Infrastructures for Digital Security in Intimate Partner Violence. In CHI Conference on Human Factors in Computing Systems. ACM, New Orleans LA USA, 1–20. https://doi.org/10.1145/3491102.3502038
- Sho Tsugawa, Yusuke Kikuchi, Fumio Kishino, Kosuke Nakajima, Yuichi Itoh, and Hiroyuki Ohsaki. 2015. Recognizing Depression from Twitter Activity. In Proceedings of the 33rd Annual ACM Conference on Human Factors in Computing Systems. ACM, Seoul Republic of Korea, 3187–3196. https://doi.org/10.1145/2702123.2702280
- Julie L. Valentine, Leslie W. Miles, Kristen Mella Hamblin, and Aubrey Worthen Gibbons. 2023. Dating App Facilitated Sexual Assault: A Retrospective Review of Sexual Assault Medical Forensic Examination Charts. Journal of Interpersonal Violence 38, 9–10 (May 2023), 6298–6322. https://doi.org/10.1177/08862605221130390
- Krishna Venkatasubramanian and Tina-Marie Ranalli. 2022. Designing Post-Trauma Self-Regulation Apps for People with Intellectual and Developmental Disabilities. In The 24th International ACM SIGACCESS Conference on Computers and Accessibility. ACM, Athens Greece, 1–14. https://doi.org/10.1145/3517428.3544798
- Charles Wilson, Donna M. Pence, and Lisa Conradi. 2013. Trauma-informed care. Encyclopedia of Social Work (2013). https://doi.org/10.1093/acrefore/9780199975839.013.1063
- Nancy S Wu, Laura C Schairer, Elinam Dellor, and Christine Grella. 2010. Childhood trauma and health outcomes in adults with comorbid substance abuse and mental health disorders. Addictive behaviors 35, 1 (2010), 68–71.
- John Zimmerman, Jodi Forlizzi, and Shelley Evenson. 2007. Research through design as a method for interaction design research in HCI. In Proceedings of the SIGCHI Conference on Human Factors in Computing Systems. ACM, San Jose California USA, 493–502. https://doi.org/10.1145/1240624.1240704
- Douglas Zytko and Nicholas Furlo. 2023. Online Dating as Context to Design Sexual Consent Technology with Women and LGBTQ+ Stakeholders. In Proceedings of the 2023 CHI Conference on Human Factors in Computing Systems(CHI ’23). Association for Computing Machinery, New York, NY, USA, 1–17. https://doi.org/10.1145/3544548.3580911
- Douglas Zytko, Nicholas Furlo, Bailey Carlin, and Matthew Archer. 2021. Computer-Mediated Consent to Sex: The Context of Tinder. Proceedings of the ACM on Human-Computer Interaction 5, CSCW1 (Apr 2021), 189:1–189:26. https://doi.org/10.1145/3449288
- Douglas Zytko, Nicholas Mullins, Shelnesha Taylor, and Richard H. Holler. 2022. Dating Apps Are Used for More Than Dating: How Users Disclose and Detect (Non-)Sexual Interest in People-Nearby Applications. Proc. ACM Hum.-Comput. Interact. 6, GROUP, Article 30 (jan 2022), 14 pages. https://doi.org/10.1145/3492849
- Douglas Zytko, Victor Regalado, Nicholas Furlo, Sukeshini A. Grandhi, and Quentin Jones. 2020. Supporting Women in Online Dating with a Messaging Interface that Improves their Face-to-Face Meeting Decisions. Proc. ACM Hum.-Comput. Interact. 4, CSCW2, Article 137 (oct 2020), 30 pages. https://doi.org/10.1145/3415208
FOOTNOTE
⁎Both authors contributed equally to this research.
Permission to make digital or hard copies of all or part of this work for personal or classroom use is granted without fee provided that copies are not made or distributed for profit or commercial advantage and that copies bear this notice and the full citation on the first page. Copyrights for components of this work owned by others than the author(s) must be honored. Abstracting with credit is permitted. To copy otherwise, or republish, to post on servers or to redistribute to lists, requires prior specific permission and/or a fee. Request permissions from permissions@acm.org.
CHI '24, May 11–16, 2024, Honolulu, HI, USA
© 2024 Copyright held by the owner/author(s). Publication rights licensed to ACM.
ACM ISBN 979-8-4007-0330-0/24/05.
DOI: https://doi.org/10.1145/3613904.3642045